Hopefully it’s not breaking news when we say URL reliability isn’t an absolute security measure. Consider homograph attacks—where malicious URLs bait users by deceptively misspelling a legitimate site (for example, being lured to mrns.com when you thought you were visiting the M&Ms site, mms.com)—or DNS hijacking, where DNS queries are resolved incorrectly so users are unknowingly redirected to infected sites.
Phishing’s nothing new, and continues to leverage a variety of tactics to trick users into divulging sensitive information, downloading, or traveling to malicious content—usually by clicking a link or opening an attached file. Browser-in-the-browser attacks are proving effective because this ploy is nearly invisible to the naked eye. As it turns out, fabricating a malicious version of a pop-up window is fairly simple with some handy HTML/CSS skills.
TechTarget projects 80% of cyber attacks this year (2022) will result from phishing scams. We’ll talk about what you need to know about this new attack method and how you can protect yourself—and your data—from a trap easily walked into if you’re not paying attention.
In this article, we’ll cover:
What Are MITB Attacks?
What Are BITB attacks?
How does BITB work?
What We’ve Seen So Far….
The Solution
What Are MITB Attacks?
A Man-in-the-browser attack is a type of Man-in-the-middle attack. When two trusting parties communicate, the attacker inserts themselves into the communication channel in between by compromising one of the party’s web browsers. They typically eavesdrop, steal data, or tamper with the session. Usually, this results in financial fraud in which internet banking services are manipulated.
For this kind of attack, they may take advantage of any security vulnerabilities or manipulate browser functionality by changing what’s on the website or getting information. Malware is an attack vector commonly used to achieve this—namely, a Trojan horse attack.
What Are BITB Attacks?
BITB attacks simulate a browser window popping up within another browser (browse-ception?) to spoof a legitimate domain. SSO (Single sign-on) is an increasingly common way users are accessing many of their sites. This attack disguises its credential theft method by appearing to be your 3rd party sign-on.
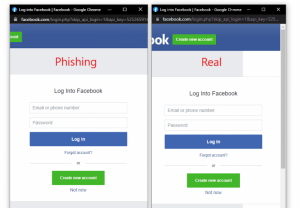
You’ve likely been through this motion. You connect to a website and a small browser window pops up and asks for Apple, Microsoft, Google, Facebook, or other credentials to log you in. You don’t have to remember, create, or reset—for the 5th time this week—yet another password for a site. Below is an image example of the nearly indistinguishable difference between a real and malicious pop-up sign-on, provided by ThreatPost.
Image courtesy of ThreatPost
How Do BITB Attacks Work?
First, like with most phishing cases, a user must visit a compromised or infected page the threat actor intends to prey from. That page contains an iframe that points to the malicious server hosting the phishing page. The pop-up page can appear on a link, button, or page-loading screen thanks to JavaScript code, which also enables the attacker to show any URL for the pop-up window.
Victims of these attacks would enter their credentials at ease because we’ve grown so familiar with this form of authentication, and it won’t broadcast a questionable URL we’ve learned to be wary of—like if we told you to come visit Blue Equinox at x%blueequinox$%%$#.com
In a BITB attack, the user is given a fraudulent pop-up window asking for their username and password. Where this differs from your everyday phishing attack is, aside from the ability to generate this popup window, this attack can display any URL it chooses for the window, including legitimate URLs. The trick some know where you hover over a link to check if the previewed URL “seems legit,” or reveals a suspicious string of characters you didn’t expect, won’t work.
What We’ve Seen So Far…
Google’s Threat Analysis Group has identified a known threat actor, Ghostwriter—from Belarus—who is known for deploying BITB attacks within phishing pages hosted by compromised sites. With recent attacks focused on Ukraine, we expect this method will become a more popular choice for more threat actors even after.
The Solution
Given its popularity and convenience, we’d like to avoid advising against the use of SSO altogether. Enabling MFA (multi-factor authentication) can greatly improve security for your single sign-on authentication, but can still be bypassed by attackers using malware. The best MFA solutions are going to be hardware devices or tokens, but are not the only means of protection.
Password managers can also help identify BITB attacks. The phishing page is not a real browser window, so password managers that autocomplete your credentials might not react to this window—ideally, the user notices something is amiss when their password does not populate automatically. Ultimately, an anti-phishing solution is likely your best defense, as it will report the detected threat or suspicious circumstances to your IT department or security team.
The Takeaway
At the end of the day, the safest and surest way to avoid BITB attacks follow the same practices to avoid phishing. Do not click links or file attachments if you do not know the source. Any doubt about the message or content you’re receiving, or who it is from—even if it came directly from a colleague—should encourage you to verify the sender knows it was delivered, that it was truly their delivery, and that whatever was sent is safe.
Find out how we make IT simple at Blue Equinox
Also see: